What is cybersecurity? ᐈ Yevhen Kasyanenko on cybersecurity in simple terms.
Cybersecurity is… Learn what cybersecurity is and how it protects your data 🔒 Let’s look at the basics of information security, its importance, and the current challenges in the field of cybersecurity in the world ✅

Yevhen Kasyanenko on cybersecurity and data protection in simple terms.
Kasyanenko Yevhen on cybersecurity and data protection in simple terms.
Good day to everyone. This is Kasyanenko Yevhen again, and today I will talk to you about cybersecurity. We will explore what it is, why it is necessary, and what aspects it includes.
What is cybersecurity?
Let’s start, as always, with a moment of theory. What is cybersecurity?
Cybersecurity is a set of technologies, processes, and methodologies aimed at achieving the highest level of protection for computers, networks, and software from hacking, cyberattacks, unauthorized access, damage, or theft of data.
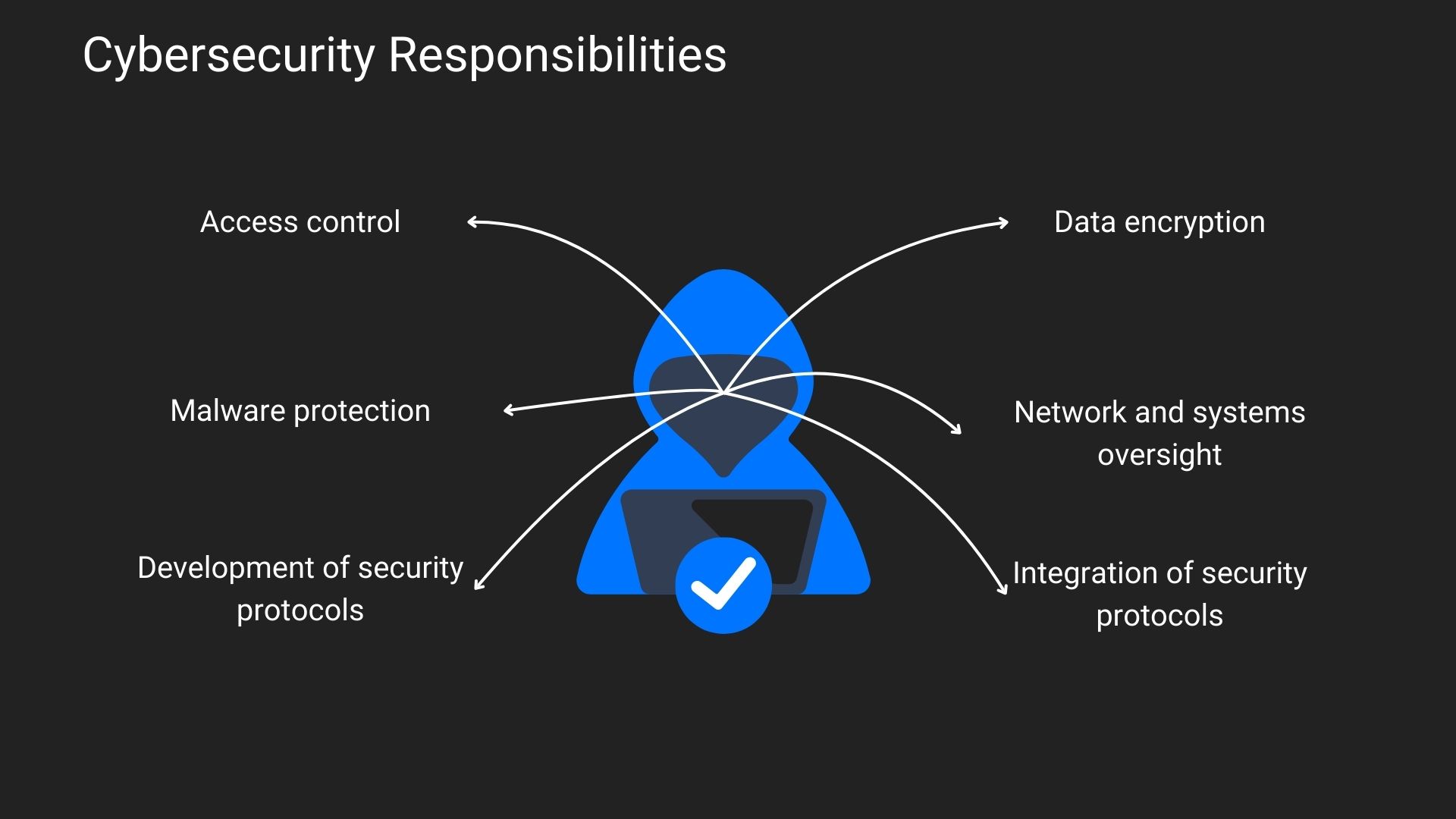
The tasks of cybersecurity include:
- protection against malware;
- data encryption;
- access management;
- network and system monitoring;
- development of security policies;
- integration of security policies.
Contact Us
Cybersecurity has several main areas and features. Let’s talk about them now.
Database protection is the primary area in the cybersecurity sector. It is responsible for ensuring the confidentiality, integrity, and availability of data. Data protection involves encryption, control, data backup, and regular access monitoring.
The next area is IAM. This is a system for managing access to systems and data based on the level of trust and user rights. Let’s put it simply. IAM includes various authentication methods, such as two-factor authentication and access rights management (when you share access with other users or company employees).
The third area is threat detection and prevention. It includes:
- comprehensive system analysis for anomalies;
- system checks for suspicious activity;
- system analysis for potential threats;
- selection and use of antivirus software;
- selection and use of firewalls and intrusion prevention systems (IPS).
Each area has its own tasks and functions. Besides the areas themselves, there are also a number of general processes that one should know (or have some understanding of).
- Incident response. The process of responding to any cyber incidents. These may include: detection, isolation, investigation, and data recovery.The team must have an action plan ready for each situation.
- Training and employee awareness. Employees need to be trained on the basics of cybersecurity. The human factor is the weakest link in the digital system.
- Compliance with regulatory requirements. There are three standards: GDPR, HIPAA, PCI DSS. Failing to comply can result in fines, loss of customer trust, and valuable data (due to gaps in the protection system).
- Risk management. An important skill that helps assess and manage risks in cybersecurity effectively. Risk management includes developing strategies to minimize risks from various types of threats.
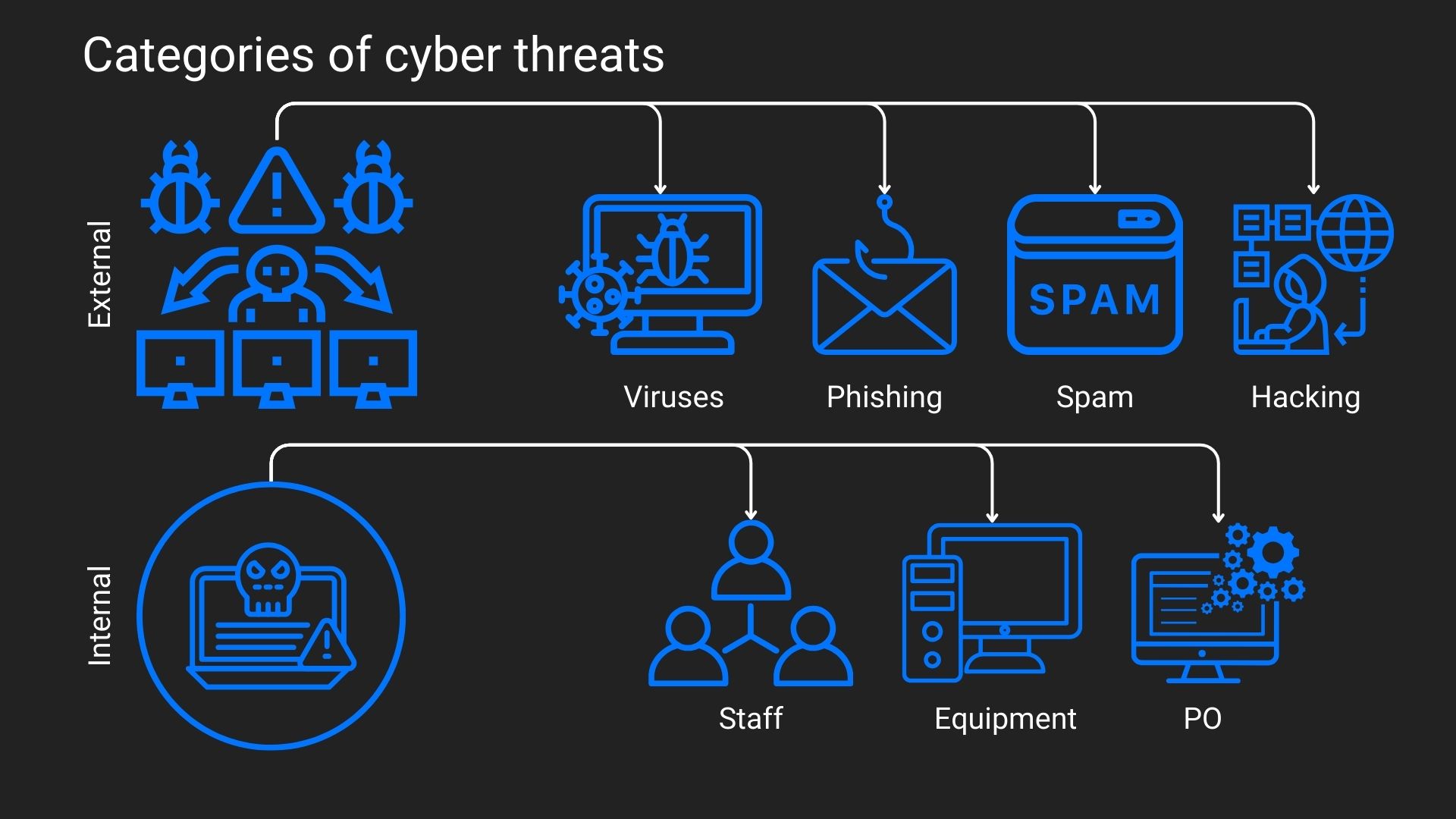
Cybersecurity and information security. Is there any difference?
Despite the fact that the terms “cybersecurity” and “information security” may seem similar to some, this is not the case. They have a number of very important differences.
Focus of work.
- Cybersecurity. The focus is on protecting data, systems, and networks of companies. Cybersecurity deals with all network threats: from hackers to viruses and phishing.
- Information security. Focuses on protecting all types of information (both in the digital environment and in the real world).
Scope of application.
- Cybersecurity. Aimed at protecting systems and data that operate in local networks (within the company, for example) or on the internet.
- Information security. Includes both digital data and paper documents, physical data carriers.
Type of threats.
- Cybersecurity. Fights against threats, attacks, and data leaks in the digital environment.
- Information security. Protects information from both internet threats and software hacking attempts, as well as from the theft of physical data and carriers.
Data protection methods.
- Cybersecurity. Uses firewalls, antivirus software, intrusion detection systems, and data encryption.
- Information security. Includes not only digital security but also physical protection options: access control, surveillance systems, and facility protection.
Legal aspects.
- Cybersecurity. Regulated by legal frameworks and regulations related to data protection and prevention of cyberattacks GDPR and HIPAA.
- Information security. Operates according to laws and standards for protecting physical data and documents + the legal/regulatory framework for cybersecurity.
System management.
- Cybersecurity. A specialized team handles management.
- Information security. Includes not only the IT sector but also managers, legal, and HR departments.
Cybersecurity Workflow: Protecting Your Business Step by Step
Summarizing the above, cybersecurity is a part of information security.
Protection of Network Infrastructure
Network structures are the most vulnerable area of the system. They are more frequently subjected to attacks by fraudsters. This is why protecting network infrastructure is so important for companies. Let me tell you how the security system for networks is built and what is used to create it.
A firewall or network firewall is responsible for filtering traffic, both incoming and outgoing. It can be considered the first line of defense for the system.
The next layer of protection is intrusion detection and prevention systems (IDS/IPS). These systems are responsible for checking traffic for suspicious activity. This helps prevent intrusions into the system from the outside.
The next step is data encryption. Data is encrypted using SSL/TLS protocols. They protect data from interception.
Another component of the protection system is network segmentation. When the network is divided into different segments, it becomes harder for fraudsters to access vulnerable information.
Actions and mechanisms that help improve the protection system:
- Network access control (NAC) is responsible for controlling the devices and users that have access to the network. Thanks to NAC, unauthorized users and devices cannot connect to the network. This method significantly reduces the likelihood of sensitive data leaks.
- Traffic analysis is a mandatory component of the security system. When your traffic is under constant monitoring and analysis, it becomes easier to identify anomalies. This means it’s easier to identify potential threats and take measures to eliminate them.
- A set of measures to protect against DDoS attacks. Why is DDoS so dangerous? It can easily overload and crash the network. Then the user simply won’t have access to the resource. To counter such attacks, various solutions are used that filter incoming traffic and weed out threats.
- And the last, but not least, function is NFV or network function virtualization. What does it do? NFV allows deploying network functions such as routing, filtering, and encryption as software.
Why is it necessary to work with experienced teams?
As you can see, the field is very broad, and the number of threats is only increasing. If you want to enhance the protection of your business, you will need an experienced team to implement the protection system. What can experts in the field offer you?
- A professional team has more experience working with various threats and types of attacks. Experience in the field helps to effectively eliminate problems and vulnerabilities in the system. An experienced team can create a unique protection strategy tailored to your needs and business specifics.
- The team of specialists uses only current technological solutions. The professional team invests resources in their training and works with the latest security tools. Novices do not have access to such a pool of opportunities, tools, and resources.
- Professionals not only integrate new solutions into the system but also support them on a long-term basis. If you work with professionals, you can be sure that your protection is always up to date.
- Specialists can act unconventionally, developing unique solutions for your needs.
- Working with professionals reduces risks and financial costs. When you hire a team of specialists, they conduct an audit of your system, make calculations, and are ready to provide you with timelines and cost estimates. You receive an analytical report, a work plan, exact costs, and deadlines for completion.
Why is K.I.S.S. Software the best in the field of cybersecurity?
Do you want to improve the security performance of your system and business? The K.I.S.S. Software team is at your service. Why do people choose us? Let me explain.
- In the process of working with clients, we consider not only the wishes and technical specifications of the client but also the specifics of the business, conducting an analysis of the current security system and its gaps.
- During the work, we use new digital solutions and technological stacks to meet market trends and requirements.
- We value honest feedback. Honesty and openness during collaboration help make timely adjustments to the project and achieve the desired result.
- You will be able to monitor the task completion process. The Kiss.software team regularly holds meetings and calls to demonstrate the current results of the work and make adjustments.
- Long-term support and updating of the security system. Your system will always be up to date and effective.
If I have intrigued you and you are interested in consulting with our experts and team in the field of cybersecurity, please leave a request for feedback, and we will contact you to arrange a meeting.