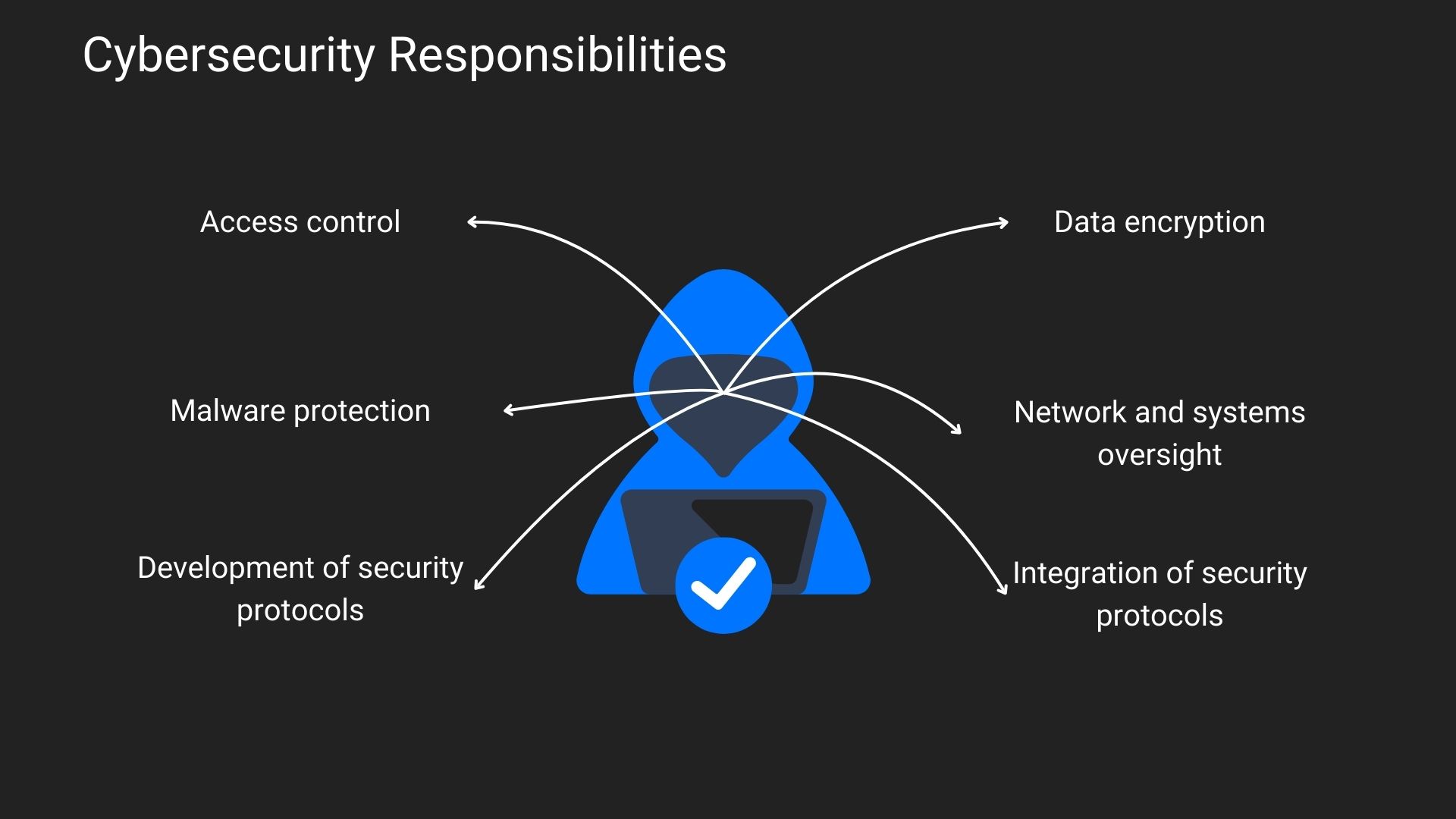
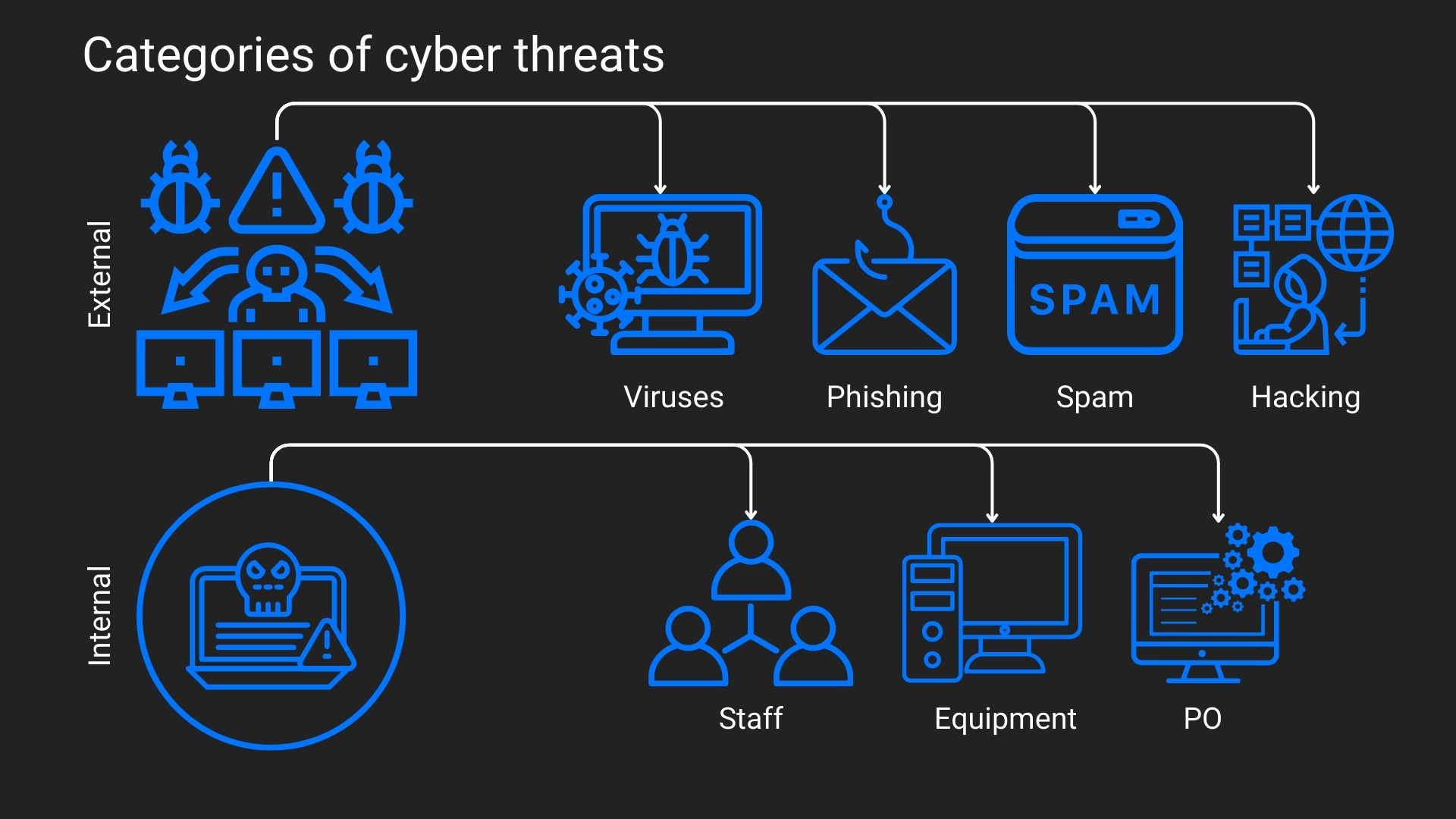
Summarizing the above, cybersecurity is a part of information security.
Protection of Network Infrastructure
Network structures are the most vulnerable area of the system. They are more frequently subjected to attacks by fraudsters. This is why protecting network infrastructure is so important for companies. Let me tell you how the security system for networks is built and what is used to create it.
A firewall or network firewall is responsible for filtering traffic, both incoming and outgoing. It can be considered the first line of defense for the system.
The next layer of protection is intrusion detection and prevention systems (IDS/IPS). These systems are responsible for checking traffic for suspicious activity. This helps prevent intrusions into the system from the outside.
The next step is data encryption. Data is encrypted using SSL/TLS protocols. They protect data from interception.
Another component of the protection system is network segmentation. When the network is divided into different segments, it becomes harder for fraudsters to access vulnerable information.
Actions and mechanisms that help improve the protection system:
- Network access control (NAC) is responsible for controlling the devices and users that have access to the network. Thanks to NAC, unauthorized users and devices cannot connect to the network. This method significantly reduces the likelihood of sensitive data leaks.
- Traffic analysis is a mandatory component of the security system. When your traffic is under constant monitoring and analysis, it becomes easier to identify anomalies. This means it's easier to identify potential threats and take measures to eliminate them.
- A set of measures to protect against DDoS attacks. Why is DDoS so dangerous? It can easily overload and crash the network. Then the user simply won't have access to the resource. To counter such attacks, various solutions are used that filter incoming traffic and weed out threats.
- And the last, but not least, function is NFV or network function virtualization. What does it do? NFV allows deploying network functions such as routing, filtering, and encryption as software.
Why is it necessary to work with experienced teams?
As you can see, the field is very broad, and the number of threats is only increasing. If you want to enhance the protection of your business, you will need an experienced team to implement the protection system. What can experts in the field offer you?
- A professional team has more experience working with various threats and types of attacks. Experience in the field helps to effectively eliminate problems and vulnerabilities in the system. An experienced team can create a unique protection strategy tailored to your needs and business specifics.
- The team of specialists uses only current technological solutions. The professional team invests resources in their training and works with the latest security tools. Novices do not have access to such a pool of opportunities, tools, and resources.
- Professionals not only integrate new solutions into the system but also support them on a long-term basis. If you work with professionals, you can be sure that your protection is always up to date.
- Specialists can act unconventionally, developing unique solutions for your needs.
- Working with professionals reduces risks and financial costs. When you hire a team of specialists, they conduct an audit of your system, make calculations, and are ready to provide you with timelines and cost estimates. You receive an analytical report, a work plan, exact costs, and deadlines for completion.
Why is K.I.S.S. Software the best in the field of cybersecurity?
Do you want to improve the security performance of your system and business? The K.I.S.S. Software team is at your service. Why do people choose us? Let me explain.
- In the process of working with clients, we consider not only the wishes and technical specifications of the client but also the specifics of the business, conducting an analysis of the current security system and its gaps.
- During the work, we use new digital solutions and technological stacks to meet market trends and requirements.
- We value honest feedback. Honesty and openness during collaboration help make timely adjustments to the project and achieve the desired result.
- You will be able to monitor the task completion process. The Kiss.software team regularly holds meetings and calls to demonstrate the current results of the work and make adjustments.
- Long-term support and updating of the security system. Your system will always be up to date and effective.
If I have intrigued you and you are interested in consulting with our experts and team in the field of cybersecurity, please leave a request for feedback, and we will contact you to arrange a meeting.